A Wi-Fi password is a very sought-after item. It’s likely that if one hosts guests at home, most of them will ask for the Wi-Fi password. People can share their Wi-Fi password using a feature on their iPhone. Users have the option of sharing their password with anyone, including those with an iPad, iPhone, or MacBook. Who knows how? Follow these instructions, but before you do, consider these considerations.You can disclose your password to anyone, including those in possession of an iPad, iPhone, or MacBook.
Also Read: 3 Simple Ways to Unlock Apple ID in 2022
- Ensure that iOS, iPadOS, or macOS are all up to date on both devices.
- Make sure they are in the contact list if one wishes to share their Wi-Fi password with others.
- Bluetooth and Wi-Fi should be enabled on both devices.
- If either device’s Personal Hotspot is active, turn it off.
- Do make sure that the other person’s Contacts have the email address that they use for their Apple ID saved.
- Be sure to save their email address in your Contacts as well.
- Verify the device is unlocked and connected to the Wi-Fi network before sharing the password.
- Keep Bluetooth and Wi-Fi ranges on the other person’s device close by.
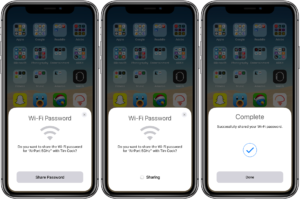
To share the Wi-Fi password, just adhere to these two easy steps.
- On the device you wish to connect to, select the Wi-Fi network.
- Tap Share Password and then tap Done on the device.
Keep in mind that unless and until the person’s email address is saved in your contacts, the option won’t be available. This means that it is not an “automatic” feature that operates only for a small group of people and appears whenever it is needed.
Then, all you have to do is adhere to these instructions if you want to change the wifi networks from which your iPad receives access.




